
DASA Intelligent Continuous Security Principles
ICS principles complement established DevSecOps and SecOps
practices. They are collectively exhaustive yet mutually exclusive,
forming a cohesive foundation for responsible and adaptive ICS
implementation. The principles outlined below serve as a
roadmap for organizations to embed security as a continuous,
automated, and integrated element of their operations.
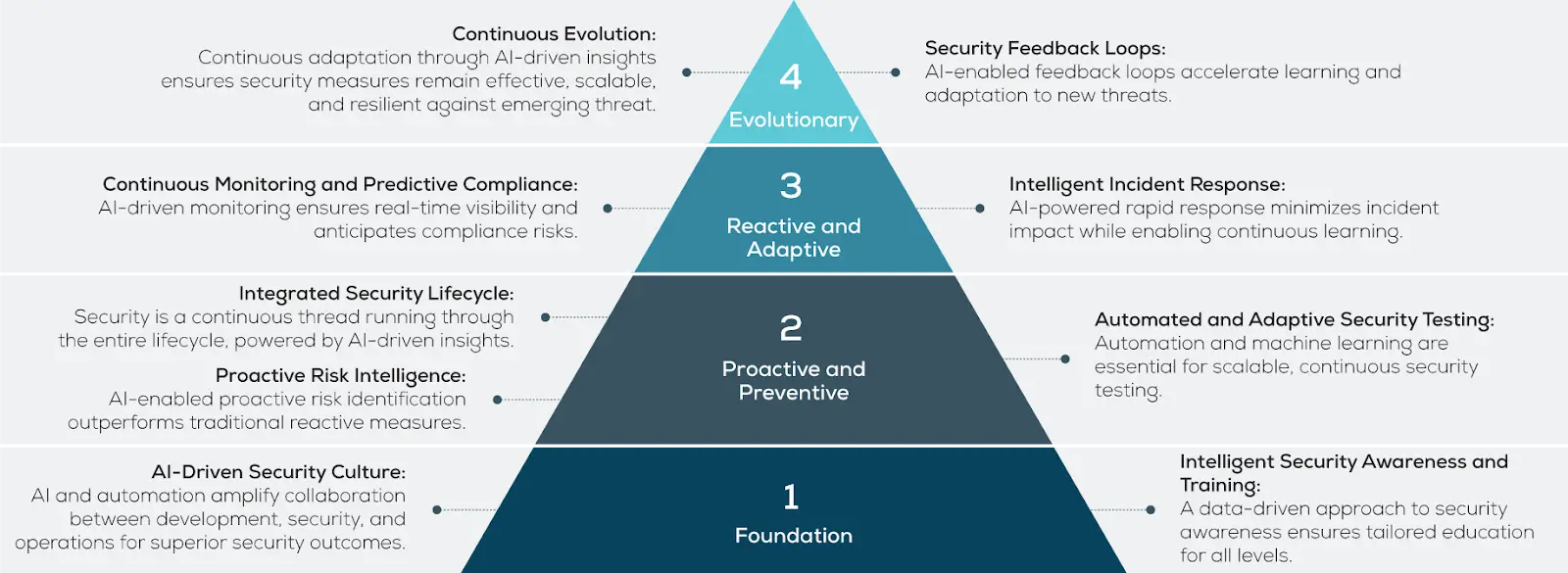
The ICS principles are grouped to align with their functional purpose
and phase in security management:
- Foundational Principles: Establish the groundwork for
collaboration, tailored training, and a shared security culture. - Proactive & Preventive Principles: Focus on anticipating and
mitigating risks, embedding security into the lifecycle, and
automating testing. - Reactive & Adaptive Principles: Enable rapid response to
incidents and iterative learning for improved resilience. - Evolutionary Principles: Drive continuous improvement
through monitoring, compliance, and adaptive feedback loops.
Foundational Principles of ICS
These principles provide the cultural and operational foundation for implementing ICS. They focus on creating a security-conscious environment and aligning organizational practices to treat security as a shared responsibility.
- AI-Driven Security Culture: Builds a collaborative environment by integrating AI-driven insights into workflows and promoting transparency across teams.
- Intelligent Security Awareness and Training: Provides tailored, role-specific security education to empower individuals at all organizational levels.
Why is it categorized as foundational?
These principles set the stage for a unified security culture and awareness, enabling effective collaboration and a shared commitment to security.
AI-Driven Security Culture
Principle: AI and automation amplify collaboration between development, security, and operations for superior security outcomes.
Challenges:
- Limited cross-team understanding of AI-driven tools.
- Resistance to adopting AI-based systems.
- Inconsistent metrics for success across teams.
Solutions:
- Provide AI-powered dashboards to promote transparency.
- Use collaborative tools integrated into workflows.
- Define shared objectives and success metrics for all teams.
Best Practices:
- Facilitate workshops on AI capabilities.
- Adopt platforms that provide real-time insights for all stakeholders.
- Build a culture of continuous learning with AI-driven feedback loops.
Intelligent Security Awareness and Training
Principle: A data-driven approach to security awareness ensures tailored education for all levels.
Challenges:
- Training fatigue due to generic content.
- Lack of contextual relevance for varying roles.
- Difficulty in measuring training effectiveness.
Solutions:
- Use AI to personalize training based on role-specific risk profiles.
- Incorporate real-world simulations.
- Implement metrics to track knowledge retention and application.
Best Practices:
- Use regularly updated training modules based on evolving threats.
- Leverage AI for dynamic phishing simulations.
- Conduct post-training assessments and refine training plan as per results.
Proactive & Preventive Principles of ICS
These principles aim to proactively identify and prevent vulnerabilities using AI and automation to reduce risks before they materialize.
- Integrated Security Lifecycle: Embeds security throughout the development lifecycle to proactively address vulnerabilities from design to deployment.
- Automated and Adaptive Security Testing: Ensures continuous, scalable testing that evolves with emerging threats.
- Proactive Risk Intelligence: Leverages AI to identify and prioritize risks dynamically, ensuring organizations stay ahead of attackers.
Why is it categorized as proactive and preventive?
These principles focus on preemptive measures, ensuring risks are minimized before they can escalate, thus supporting a forward-looking security strategy.
Integrated Security Lifecycle
Principle: Security is a continuous thread running through the entire lifecycle, powered by AI-driven insights.
Challenges:
- Integrating security into fast-paced CI/CD environments.
- Resistance from developers viewing security as a hindrance.
- Lack of standardized security protocols across teams.
Solutions:
- Use AI-driven tools to identify vulnerabilities during coding and deployment.
- Automate compliance checks and vulnerability scans.
- Encourage adoption with seamless integration into existing CI/CD tools.
Best Practices:
- Conduct real-time static and dynamic code analysis.
- Employ AI to simulate potential vulnerabilities in early design stages.
- Continuously monitor and update security measures post-deployment.
Automated and Adaptive Security Testing
Principle: Automation and machine learning are essential for scalable, continuous security testing.
Challenges:
- High initial cost of automation tools.
- Difficulty in keeping tests updated with evolving threats.
- Ensuring reliability across distributed systems.
Solutions:
- Start with automating high-risk areas and expand incrementally.
- Use AI to adapt test scenarios based on real-time data.
- Integrate testing tools directly into CI/CD pipelines.
Best Practices:
- Conduct continuous security testing for every code commit.
- Use machine learning to predict potential test scenarios.
- Automate regression testing to validate security patches.
Proactive Risk Intelligence
Principle: AI-enabled proactive risk identification outperforms traditional reactive measures.
Challenges:
- Limited access to quality threat intelligence data.
- Overwhelming volume of potential risk signals.
- Difficulty in prioritizing risks effectively.
Solutions:
- Use AI-driven analytics to consolidate and prioritize risk data.
- Leverage external threat intelligence feeds to augment internal insights.
- Implement tiered alerting systems to reduce noise.
Best Practices:
- Continuously update models with new data.
- Simulate attack scenarios to evaluate system resilience.
- Monitor risks with AI-enabled threat-hunting tools.
Reactive & Adoptive Principles of ICS
These principles enable organizations to respond swiftly to incidents and adapt their defenses based on lessons learned.
- Principles:
- Intelligent Incident Response: Uses AI to automate and accelerate incident detection, containment, and resolution.
- Continuous Monitoring and Predictive Compliance: Uses AI-driven monitoring for real-time visibility and predictive compliance management.
Why is it categorized as reactive and adaptive?
These principles focus on limiting the impact of incidents and leveraging them as opportunities for improvement, ensuring the organization remains resilient.
Intelligent Incident Response
Principle: AI-powered rapid response minimizes incident impact while enabling continuous learning.
Challenges:
- Slow response times due to manual processes.
- Inconsistent incident resolution strategies.
- Difficulty in learning from past incidents.
Solutions:
- Use AI to analyze incidents and suggest next steps.
- Automate containment and remediation processes where possible.
- Develop post-incident review frameworks powered by AI.
Best Practices:
- Conduct incident drills to refine response strategies.
- Use Generative AI for scenario planning.
- Automate root cause analysis to inform future responses.
Continuous Monitoring and Predictive Compliance
Principle: AI-driven monitoring ensures real-time visibility and anticipates compliance risks.
Challenges:
- Maintaining visibility across hybrid environments.
- Keeping up with evolving regulatory requirements.
- Identifying compliance gaps in real-time.
Solutions:
- Deploy AI tools for continuous monitoring and anomaly detection.
- Automate compliance checks aligned with updated regulations.
- Use predictive analytics to address potential non-compliance risks.
Best Practices:
- Implement unified monitoring platforms.
- Regularly review compliance dashboards.
- Conduct audits to ensure AI-driven insights align with regulatory expectations.
Evolutionary Principles of ICS
The evolutionary principles ensure continuous adaptation and improvement in security measures to keep pace with emerging threats.
Security Feedback Loops and Continuous Evolution: Accelerates learning and adaptation by leveraging AI-enabled feedback loops from past incidents.Focuses on adapting defenses to remain scalable, resilient, and effective.
Why is it categorized as evolutionary?
These principles focus on iterative improvements, ensuring security evolves continuously to remain effective and relevant in a changing threat landscape.
Security Feedback Loops and Continuous Evolution
Principle: AI-enabled feedback loops accelerate learning and adaptation to new threats.
Challenges:
- Inconsistent incident data collection.
- Resistance to adopting iterative improvement processes.
- Limited resources for analyzing feedback effectively.
Solutions:
- Automate feedback collection and analysis using AI tools.
- Create iterative improvement plans informed by actionable insights.
- Celebrate incremental wins to encourage team buy-in.
Best Practices:
- Use post-incident reviews to inform updates.
- Simulate future attack scenarios to test system adaptability.
- Monitor KPIs likeMean Time to Detect( MTTD) and Mean Time to Respond(MTTR) to measure progress.
By adopting these principles, businesses can build resilient, compliant, and innovative environments capable of thriving in the modern threat landscape.
