Security professionals not only have the challenge of protecting their organizations against emerging threats but also to adapt and innovate continuously. The Seven-Step Transformation Blueprint provides a structured, systematic approach to transitioning from traditional, siloed security models to a dynamic, AI-assisted security framework. This blueprint is designed to integrate security, development, and operational practices into a unified, proactive strategy that embodies the principles of Intelligent Continuous Security™ (ICS).
At its core, the blueprint emphasizes that security is not a one-time project but a journey of continuous improvement. The triple infinity symbol that accompanies this framework symbolizes the perpetual advancement of people, processes, and technology—a reminder that transformation is an ongoing pursuit.
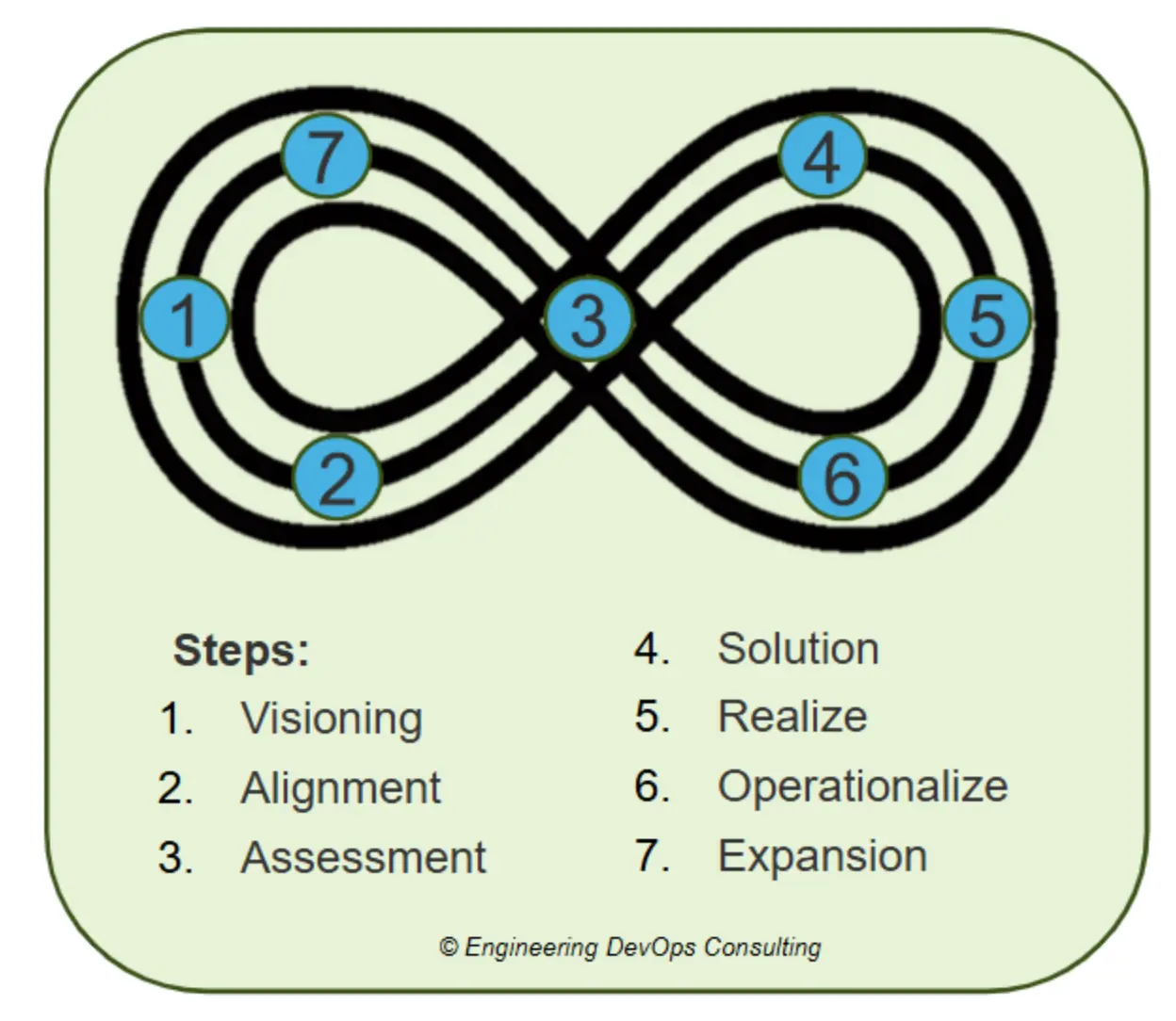
Step 1: Visioning
The first step in the transformation process is to establish a clear and compelling vision. For security professionals, this means defining the strategic direction and identifying the leadership that will champion the change. During the Visioning phase, organizations must:
- Identify transformation leaders: Select key sponsors and strategic leaders who are committed to driving the ICS transformation forward. These individuals will be responsible for setting the tone and ensuring that security remains a top organizational priority.
- Define strategic goals: Establish a set of measurable, strategic goals that reflect the desired future state of your security operations. These goals should align with broader business objectives and address both current challenges and anticipated future threats.
- Select target applications: Identify specific applications or systems that will be transformed first. This targeted approach helps in focusing resources and establishing a proof of concept for broader deployment.
- Develop foundational documents: Create essential deliverables such as an ICS Transformation Scorecard and a strategic goals document to guide the process.
Key Deliverables:
- Transformation leadership team: A select group of strategic leaders driving the ICS transformation to secure top-level commitment and alignment.
- Selected applications for transformation: Identified critical systems to pilot changes, focusing efforts for measurable, impactful results.
- ICS transformation scorecard: A performance tool tracking ICS maturity that provides quantifiable benchmarks for progress.
- Strategic goals document: A clear statement of objectives and tactics to align and guide the security transformation with overall business strategy.
- Committed next steps: Defined initial actions that ensure sustained momentum and accountability throughout the transformation.
Step 2: Alignment
Alignment is crucial to ensure that all stakeholders are on board and working in accordance with the Strategic goals document. In this step, the transformation leadership works to build consensus and create a unified approach and shared commitment in support of the transformation. Key activities include:
- Building the ICS transformation team: Assemble an ICS Transformation Team that includes leaders and key team members from across the organization. This team will be instrumental in executing the vision.
- Establishing specific goals: For each selected application, the team translates the Strategic goals from step 1 into clear, application-specific goals that will drive the transformation for the specific applications the team is responsible for.
- Promoting a collaborative culture: Encourage open dialogue among teams and stakeholders to foster a culture of collaboration and shared responsibility in achieving the transformation objectives.
Key Deliverables (for each selected application):
- Defined transformation team
- Specific transformation goals:Detailed objectives for each application that drive focused and measurable improvements.
- Agreed next steps:Consensus-driven immediate actions that maintain project momentum and collective accountability.
The article continues below the Related guidance
Certification
DASA Intelligent Continuous Security™ Certification Program
Value Box
DASA Intelligent Continuous Security™ Value Box
Step 3: Assessment
Before any changes can be made, it’s essential to understand the current state of your security practices. The Assessment step involves a deep dive into existing security practices (inclusive of people, process, and technologies), maturity levels, and overall readiness for transformation:
- Current state analysis: Document the existing state of selected applications, identifying strengths, weaknesses, and areas for improvement.
- Maturity assessments: Conduct thorough gap assessments of current ICS practices to understand where your organization stands in terms of technology, process, and people relative to organization priorities and known good practices.
- Deep-dive evaluations: Analyze specific topics in detail to uncover vulnerabilities and gaps in security practices.
- Value-stream mapping: Develop a current state value-stream map that reflects how well security processes currently align with organizational goals and where there are opportunities for improvement.
- Stakeholder alignment: Ensure that all relevant stakeholders are engaged in defining solution requirements based on the current state analysis.
Key Deliverables (for each selected application):
- Detailed Current state description: A comprehensive analysis of existing security practices that identifies strengths and areas for improvement.
- Maturity assessment of ICS practices: An evaluation that highlights current capability gaps and readiness for transformation.
- Current state value-stream map: A visual mapping of current processes that exposes inefficiencies and optimization opportunities.
- Prioritized list of solution requirements: A ranked inventory of security needs that directs focus to high-impact transformation areas.
Step 4: Solution
In the Solution step, organizations focus on designing an ICS solution that meets the requirements from Step 3.
- Future state value-stream mapping: Create a future state value-stream map that visualizes the desired solution requirements inclusive of people, process and technologies.
- Solution roadmap development: Formulate a detailed roadmap that outlines themes, epics, and user stories. This roadmap serves as a blueprint for the transformation.
- ROI analysis: Develop a robust ROI case to justify the transformation investment, demonstrating values that the new security posture will generate for the organization over an investment period.
- Leadership alignment: Secure final buy-in from senior leadership by presenting the solution recommendation along with detailed cost-benefit analyses.
Key Deliverables (for each selected application):
- Future state value-stream map: A forward-looking process visualization that guides the organization toward meeting the strategic goals and ICS transformation requirements
- Tool and technology recommendations: Curated solutions that align with the ICS transformation requirements.
- Comprehensive transformation roadmap: A detailed,organized plan with phases and milestones that provides clear guidance for orchestrating and monitoring the ICS transformation.
- Backlog of themes, epics, and user stories: Prioritized, manageable initiatives that guide management of the ICS transformation activities.
- ROI estimates:Financial projections that justify the value and cost-effectiveness of the transformation..
- Final solution recommendation and leadership alignment
Step 5: Realize
The Realize step transforms the activities defined in step 4 to a working solution . Here, the transformation teams implement solution components, and validate new solutions through controlled pilots:
- Implementation of user stories: Develop, deploy and validate solutions according to the user stories in accordance with the plan from step 4.
- Proof of concept (POC) trials: Execute POC trials to test and validate solutions against real-world security use cases, ensuring they meet the requirements established in the prior steps.
- Training and enablement: Roll out training programs concurrently with the deployment of new solutions to ensure that teams are well-prepared to adopt and manage the changes.
- Governance activation: Initiate governance practices to monitor the rollout, address issues promptly, and ensure compliance with security policies.
Key Deliverables (for each selected application):
- Working software: code and operational software that meets the requirement defined in the prior steps.
- Successful POC trials:Pilot tests validating technology solutions meet the requirement defined in the prior steps.
- Production release: Documented, executed changes integrated into live systems, showcasing tangible progress.
- Comprehensive training sessions: Structured programs that equip teams to effectively adopt and manage new ICS solutions.
- Activated governance protocols: Established oversight mechanisms that ensure ongoing compliance and effective management.
Step 6: Operationalize
Step 6 is where the solution from step 5 is made ready for large-scale operations. This phase ensures that ICS solutions are suitable for operations at scale.
- Controlled access and rollout: Implement access controls and phased rollout processes to ensure that solution updates can be deployed successfully and with manageable risk.
- Continuous monitoring: Set up robust monitoring systems to track performance, detect anomalies, and ensure that security measures are effective.
- Governance and support: Establish ongoing governance and support structures to maintain the new security posture, providing a framework for managing issues and ensuring compliance.
- Process evolution: Design processes that are flexible and capable of evolving as new threats emerge and technologies advance.
Key Deliverables (for each selected application):
- Secure, controlled access mechanisms:Systems that ensure only authorized access, safeguarding new solutions and data integrity.
- Comprehensive monitoring systems: Tools that provide real-time performance tracking and robust security oversight.
- Established governance protocols:Formal rules that maintain compliance and effectively manage ongoing operations.
- Reliable support structures: Dedicated teams and processes that offer continuous operational and technical assistance.
- Defined evolution strategies:Ongoing plans that ensure the security framework remains agile and future-proof.
Step 7: Expansion
The final step in the transformation process is to expand the benefits across the organization and to foster a culture of continuous improvement:
- Best practice sharing: Proactively share proven engineering and security practices across departments and teams.
- Scaling successful solutions: Extend the successful transformation solutions to additional applications, adapting them to various pipeline variations and deployment regions.
- Strategic portfolio management: Implement horizontal and vertical transformation plans that ensure continuous optimization and prepare the organization for next-generation security challenges.
- Continuous optimization: Establish processes for ongoing evaluation and improvement, ensuring that the security framework remains robust and responsive over time.
Key Deliverables (for all applications):
- Strategic portfolio management framework: A system for prioritizing and managing multiple initiatives to optimize resource use.
- Detailed horizontal and vertical transformation plans:Strategies to scale best practices across functions and all organizational levels.
- Continuous optimization strategies:Ongoing evaluation methods that adapt and enhance the security posture in response to emerging threats.
Conclusion
For security professionals, the Seven-Step Transformation Blueprint offers a clear and methodical pathway to achieving Intelligent Continuous Security. By moving through the stages of Visioning, Alignment, Assessment, Realize, Solution, Deployment, and Expansion, organizations can transform their security posture from reactive to proactive. This structured approach not only addresses current vulnerabilities but also builds a resilient, AI-powered security framework that evolves with emerging threats.
As the threat landscape continues to change, embracing such a comprehensive transformation blueprint is critical. It enables security teams to anticipate risks, integrate advanced technologies, and foster a culture of continuous improvement—ensuring that your organization remains secure, agile, and ready for the challenges of tomorrow.
Intelligent Continuous Security is a Trademark of Engineering DevOps Consulting.
